|
FFIEC
information technology audits
-
As a former bank examiner
with over 40 years IT audit experience, I will bring an examiner's
perspective to the FFIEC information technology audit for bankers in
Texas, New Mexico, Colorado, and Oklahoma.
For more information go
to
On-site FFIEC IT Audits.
FYI
- Company sues worker who fell for email scam - An office worker who
transferred her employer's cash to an online fraudster allegedly
ignored a warning telling her she was falling victim to a scam.
https://www.bbc.com/news/uk-scotland-glasgow-west-47135686
Gov. Newsom proposes ‘data dividend’ for Calif. consumers -
California May have some of the strictest data privacy and security
laws on the books, but Gov. Gavin Newsom has floated a “new data
dividend” that would compel Google, Facebook and the like to pay
consumers in the state who choose to share their data.
https://www.scmagazine.com/home/security-news/gov-newsom-proposes-data-dividend-for-calif-consumers/
How to build privacy for security and achieve sustained compliance -
Global and domestic privacy regulations like GDPR and the California
Consumer Privacy Act (CCPA) are forcing businesses to develop and
implement comprehensive data management processes to comply with new
privacy requirements.
https://www.scmagazine.com/home/opinion/how-to-build-privacy-for-security-and-achieve-sustained-compliance/
Israeli cyber-hotline offers help for the hacked - Israel has
launched a cyber hotline, staffed mostly by veterans of military
computing units, to enable businesses and private individuals to
report suspected hacking and receive real-time solutions.
https://www.reuters.com/article/us-cyber-israel-hotline/israeli-cyber-hotline-offers-help-for-the-hacked-idUSKCN1Q70K1
US needs an internet data privacy law, GAO tells Congress - Chief
auditor cites Facebook's Cambridge Analytica data scandal as an
example of why a privacy law is necessary.
https://www.cnet.com/news/us-needs-an-internet-data-privacy-law-gao-tells-congress/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Image-I-Nation supply chain breach exposes data of major credit
agencies’ customers - Image-I-Nation Technologies, Inc., which
provides hosting services and software to consumer reporting
agencies like Equifax, Experian and TransUnion, experienced a supply
chain breach that left users’ personal information exposed for as
long as two weeks.
https://www.scmagazine.com/home/security-news/image-i-nation-supply-chain-breach-exposes-data-of-major-credit-agencies-customers/
Hackers KO Malta's Bank of Valletta in attempt to nick €13m -
Hapless bank goes into lockdown mode, vanishes from the internet -
Malta's Bank of Valetta (BOV) has pulled the plug on its entire
internet access, including shutting down cashpoints and branch
offices, after detecting a "cyber intrusion" by crims that tried to
steal nearly €13m.
https://www.theregister.co.uk/2019/02/13/bank_of_valletta_13m_euro_hackers_shutdown/
Ever used VFEmail? No? Well, chances are you never will now: Hackers
wipe servers, backups in 'catastrophic' attack - A hacker wiped
every server and backup of VFEmail this week in a "catastrophic"
attack, according to the webmail service.
https://www.theregister.co.uk/2019/02/12/vfemail_hacked_wiped/
Dunn Brothers Coffee, Holiday Inn among those exposed by third-party
payment card vendor breach - A company that handles payment
operations for a large number of hotels and food establishments,
including Holiday Inn, Dunn Brothers Coffee and Zipps Sports Grill,
is informing its customers of a data breach that may have
compromised consumer’s payment card information.
https://www.scmagazine.com/home/security-news/data-breach/dunn-brothers-coffee-holiday-inn-among-those-exposed-by-third-party-payment-card-vendor-breach/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
Introduction
Banking organizations have been delivering electronic services to
consumers and businesses remotely for years. Electronic funds
transfer, including small payments and corporate cash management
systems, as well as publicly accessible automated machines for
currency withdrawal and retail account management, are global
fixtures. However, the increased world-wide acceptance of the
Internet as a delivery channel for banking products and services
provides new business opportunities for banks as well as service
benefits for their customers.
Continuing technological innovation and competition among existing
banking organizations and new market entrants has allowed for a much
wider array of electronic banking products and services for retail
and wholesale banking customers. These include traditional
activities such as accessing financial information, obtaining loans
and opening deposit accounts, as well as relatively new products and
services such as electronic bill payment services, personalized
financial "portals," account aggregation and business-to-business
market places and exchanges.
Notwithstanding the significant benefits of technological
innovation, the rapid development of e-banking capabilities carries
risks as well as benefits and it is important that these risks are
recognized and managed by banking institutions in a prudent manner.
These developments led the Basel Committee on Banking Supervision to
conduct a preliminary study of the risk management implications of
e-banking and e-money in 1998. This early study demonstrated a clear
need for more work in the area of e-banking risk management and that
mission was entrusted to a working group comprised of bank
supervisors and central banks, the Electronic Banking Group (EBG),
which was formed in November 1999.
The Basel Committee released the EBG's Report on risk management
and supervisory issues arising from e-banking developments in
October 2000. This Report inventoried and assessed the major risks
associated with e-banking, namely strategic risk, reputational risk,
operational risk (including security and legal risks), and credit,
market, and liquidity risks. The EBG concluded that e-banking
activities did not raise risks that were not already identified by
the previous work of the Basel Committee. However, it noted that
e-banking increase and modifies some of these traditional risks,
thereby influencing the overall risk profile of banking. In
particular, strategic risk, operational risk, and reputational risk
are certainly heightened by the rapid introduction and underlying
technological complexity of e-banking activities.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION -
NETWORK ACCESS
Network security requires effective implementation of several
control mechanisms to adequately secure access to systems and data.
Financial institutions must evaluate and appropriately implement
those controls relative to the complexity of their network. Many
institutions have increasingly complex and dynamic networks stemming
from the growth of distributed computing.
Security personnel and network administrators have related but
distinct responsibilities for ensuring secure network access across
a diverse deployment of interconnecting network servers, file
servers, routers, gateways, and local and remote client
workstations. Security personnel typically lead or assist in the
development of policies, standards, and procedures, and monitor
compliance. They also lead or assist in incident-response efforts.
Network administrators implement the policies, standards, and
procedures in their day-to-day operational role.
Internally, networks can host or provide centralized access to
mission-critical applications and information, making secure access
an organizational priority. Externally, networks integrate
institution and third-party applications that grant customers and
insiders access to their financial information and Web-based
services. Financial institutions that fail to restrict access
properly expose themselves to increased transaction, reputation, and
compliance risk from threats including the theft of customer
information, data alteration, system misuse, or denial-of-service
attacks.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We continue
the series on the National Institute of Standards and Technology
(NIST) Handbook.
Chapter 19 - CRYPTOGRAPHY
19.2 Uses of Cryptography
 Cryptography
is used to protect data both
inside and outside the boundaries of a computer system. Outside the
computer system, cryptography is sometimes the
only way to
protect data. While in a computer system, data is normally protected
with logical and physical access controls (perhaps supplemented by
cryptography). However, when in transit across communications lines
or resident on someone else's computer, data cannot be protected by
the originator's logical or physical access controls. Cryptography
provides a solution by protecting data even when the data is no
longer in the control of the originator. Cryptography
is used to protect data both
inside and outside the boundaries of a computer system. Outside the
computer system, cryptography is sometimes the
only way to
protect data. While in a computer system, data is normally protected
with logical and physical access controls (perhaps supplemented by
cryptography). However, when in transit across communications lines
or resident on someone else's computer, data cannot be protected by
the originator's logical or physical access controls. Cryptography
provides a solution by protecting data even when the data is no
longer in the control of the originator.
19.2.1 Data Encryption
One of the best ways
to obtain cost-effective data confidentiality is through the use of
encryption. Encryption transforms intelligible data, called
plaintext, into
an unintelligible form, called
ciphertext. This process is reversed
through the process of decryption. Once data is encrypted, the
ciphertext does not have to be protected against disclosure.
However, if ciphertext is modified, it will not decrypt correctly.
Both secret key and public key cryptography can
be used for data encryption although not all public key algorithms
provide for data encryption.
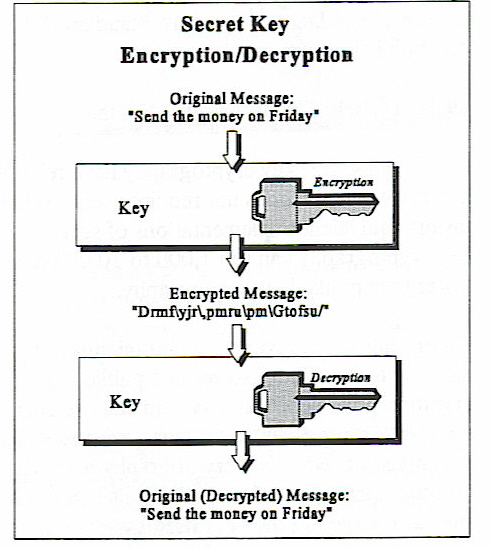
To use a secret key algorithm, data is encrypted
using a key. The same key must be used to decrypt the data.
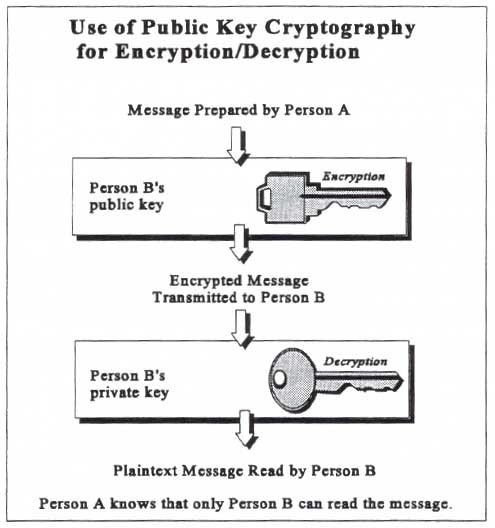 When
public key cryptography is used for encryption, any party may use
any other party's public key to encrypt a message; however, only the
party with the corresponding private key can decrypt, and thus read,
the message. When
public key cryptography is used for encryption, any party may use
any other party's public key to encrypt a message; however, only the
party with the corresponding private key can decrypt, and thus read,
the message.
Since secret key encryption is typically much
faster, it is normally used for encrypting larger amounts of data.
19.2.2 Integrity
In computer systems,
it is not always possible for humans to scan information to
determine if data has been erased, added, or modified. Even if
scanning were possible, the individual may have no way of knowing
what the correct data should be. For example, "do" may be changed to
"do not," or $1,000 may be changed to $10,000. It is therefore
desirable to have an automated means of detecting
both intentional
and unintentional modifications of data.
While error detecting codes have long been used
in communications protocols (e.g., parity bits), these are more
effective in detecting (and correcting) unintentional modifications.
They can be defeated by adversaries. Cryptography can effectively
detect both intentional and unintentional modification; however,
cryptography does not protect files from being modified. Both secret
key and public key cryptography can be used to ensure integrity.
Although newer public key methods may offer more flexibility than
the older secret key method, secret key integrity verification
systems have been successfully integrated into many applications.
When secret key
cryptography is used, a message authentication code (MAC) is
calculated from and appended to the data. To verify that the data
has not been modified at a later time, any party with access to the
correct secret key can recalculate the MAC. The new MAC is compared
with the original MAC, and if they are identical, the verifier has
confidence that the data has not been modified by an unauthorized
party. FIPS 113, Computer Data
Authentication, specifies a standard
technique for calculating a MAC for integrity verification.
Public key cryptography verifies integrity
by using of public key signatures and secure hashes. A secure hash
algorithm is used to create a message digest. The message digest,
called a hash, is a short form of the message that
changes if the message is modified. The hash is then signed with a
private key. Anyone can recalculate the hash and use the
corresponding public key to verify the integrity of the message.
|