|
FFIEC
information technology audits
-
As a former bank examiner
with over 40 years IT audit experience, I will bring an examiner's
perspective to the FFIEC information technology audit for bankers in
Texas, New Mexico, Colorado, and Oklahoma.
For more information go
to
On-site FFIEC IT Audits.
FYI
- Microsoft admits expiring-password rules are useless - Microsoft
has admitted that one of the great scourges of our time, the
password reset rule, is bunk.
https://www.cnet.com/news/kentucky-derby-horses-get-first-class-treatment-on-air-horse-one/
Washington State Legislature Passes New Data Breach Law - The
Washington legislature has passed a bill that effectively expands
the state’s consumer data breach notification requirements.
https://www.tripwire.com/state-of-security/government/washington-state-legislature-passes-new-data-breach-law/
Federal Cyber Reskilling Academy Announces Second Class - Following
strong interest from federal employees in the Federal Cyber
Reskilling Academy’s first class, the White House announced Tuesday
it is accepting applications for a second class.
https://www.nextgov.com/cybersecurity/2019/04/federal-cyber-reskilling-academy-announces-second-class/156486/
Greenville in recovery phase from Robbinhood ransomware attack - The
city of Greenville, N.C., said it is recovering from the April 10
ransomware attack that had effectively knocked the city offline,
without having to resort to paying the ransom demand.
https://www.scmagazine.com/home/security-news/ransomware/greenville-in-recovery-phase-from-robbinhood-ransomware-attack/
5 ways hackers use digital channels to launch VIP attacks - VIP
attacks target high-profile individuals like company executives,
politicians, and celebrities. For enterprise businesses, executives
present a critical target for hackers, usually because they have
access to a vast wealth of information.
https://www.scmagazine.com/home/opinion/executive-insight/5-ways-hackers-use-digital-channels-to-launch-vip-attacks/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Flaw in Columbia, S.C., website search tool exposed database, SMPT
server passwords - A misconfiguration in the search tool on the city
of Columbia, S.C. website had a security flaw that could have
exposed database and SMPT server passwords.
https://www.scmagazine.com/home/security-news/data-breach/flaw-in-columbia-s-c-website-search-tool-exposed-database-smpt-server-passwords/
Ransomware disables Cleveland airport’s email systems, information
screens - A ransomware attack reportedly has affected email, payroll
and record-keeping systems at Cleveland Hopkins International
Airport this week and also darkened the transportation facility’s
information screens.
https://www.scmagazine.com/home/security-news/ransomware-disables-cleveland-airports-email-systems-information-screens/
GandCrab ransomware strikes Doctors’ Management Services - Doctors’
Management Services (DMS) was struck with GandCrab ransomware on
Christmas Eve last year, possibly exposing the PII of its clients’
patients.
https://www.scmagazine.com/home/security-news/ransomware/gandcrab-ransomware-strikes-doctors-management-services/
Amnesty Intl. says cyberattack on Hong Kong office appears linked to
known APT group - The Hong Kong division of human rights
organization Amnesty International said yesterday that its offices
were recently targeted by a sophisticated cyberattack that bore the
hallmarks of Chinese state-sponsored actors.
https://www.scmagazine.com/home/security-news/amnesty-intl-says-cyberattack-on-hong-kong-office-appears-linked-to-known-apt-group/
Info on 80 million American households found in open database - A
cybersecurity research team has found an unidentified open database
containing 24GB of records detailing information on 80 million
American households.
https://www.scmagazine.com/home/security-news/data-breach/info-on-80-million-american-households-found-in-open-database/
Docker Hub database access compromises 190,000 accounts - Docker Hub
reported a single database was accessed by an unauthorized user on
April 25 exposing 190,000 accounts.
https://www.scmagazine.com/home/security-news/docker-hub-database-access-compromises-190000-accounts/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
While
the Board of Directors has the responsibility for ensuring that
appropriate security control processes are in place for e-banking,
the substance of these processes needs special management attention
because of the enhanced security challenges posed by e-banking.
Over the next number of weeks we will cover the principles of
Security Controls.
Board and Management Oversight
- Principle 4: Banks should
take appropriate measures to authenticate the identity and
authorization of customers with whom it conducts business over the
Internet. (Part 1 of 2)
It is essential in banking to confirm that a particular
communication, transaction, or access request is legitimate.
Accordingly, banks should use reliable methods for verifying the
identity and authorization of new customers as well as
authenticating the identity and authorization of established
customers seeking to initiate electronic transactions.
Customer verification during account origination is important in
reducing the risk of identity theft, fraudulent account applications
and money laundering. Failure on the part of the bank to adequately
authenticate customers could result in unauthorized individuals
gaining access to e-banking accounts and ultimately financial loss
and reputational damage to the bank through fraud, disclosure of
confidential information or inadvertent involvement in criminal
activity.
Establishing and authenticating an individual's identity and
authorization to access banking systems in a purely electronic open
network environment can be a difficult task. Legitimate user
authorization can be misrepresented through a variety of techniques
generally known as "spoofing." Online hackers can also take over the
session of a legitimate authorized individual through use of a
"sniffer" and carry out activities of a mischievous or criminal
nature. Authentication control processes can in addition be
circumvented through the alteration of authentication databases.
Accordingly, it is critical that banks have formal policy and
procedures identifying appropriate methodology(ies) to ensure that
the bank properly authenticates the identity and authorization of an
individual, agent or system by means that are unique and, as far as
practical, exclude unauthorized individuals or systems. Banks can us
a variety of methods to establish authentication, including PINs,
passwords, smart cards, biometrics, and digital certificates. These
methods can be either single factor or multi-factor (e.g. using both
a password and biometric technology to authenticate). Multi-factor
authentication generally provides stronger assurance.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION -
NETWORK ACCESS
Stateful Inspection Firewalls
Stateful inspection firewalls are packet filters that monitor the
state of the TCP connection. Each TCP session starts with an
initial handshake communicated through TCP flags in the header
information. When a connection is established the firewall adds the
connection information to a table. The firewall can then compare
future packets to the connection or state table. This essentially
verifies that inbound traffic is in response to requests initiated
from inside the firewall.
Proxy Server Firewalls
Proxy servers act as an intermediary between internal and external
IP addresses and block direct access to the internal network.
Essentially, they rewrite packet headers to substitute the IP of the
proxy server for the IP of the internal machine and forward packets
to and from the internal and external machines. Due to that limited
capability, proxy servers are commonly employed behind other
firewall devices. The primary firewall receives all traffic,
determines which application is being targeted, and hands off the
traffic to the appropriate proxy server. Common proxy servers are
the domain name server (DNS), Web server (HTTP), and mail (SMTP)
server. Proxy servers frequently cache requests and responses,
providing potential performance benefits. Additionally, proxy
servers provide another layer of access control by segregating the
flow of Internet traffic to support additional authentication and
logging capability, as well as content filtering. Web and e-mail
proxy servers, for example, are capable of filtering for potential
malicious code and application-specific commands.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)
20.2
HGA's Computer System
HGA relies
on the distributed computer systems and networks shown in Figure
20.1. They consist of a collection of components, some of which are
systems in their own right. Some belong to HGA, but others are owned
and operated by other organizations. This section describes these
components, their role in the overall distributed system
architecture, and how they are used by HGA.
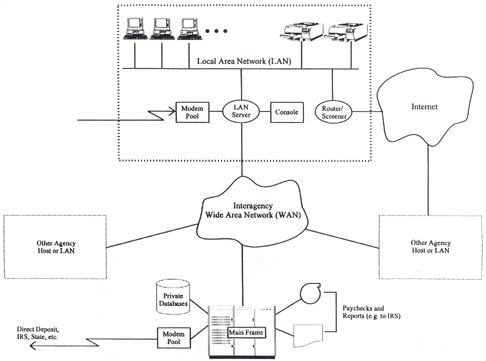
Figure 20.1
|