|
FFIEC
information technology audits
-
As a former bank examiner
with over 40 years IT audit experience, I will bring an examiner's
perspective to the FFIEC information technology audit for bankers in
Texas, New Mexico, Colorado, and Oklahoma.
For more information go
to
On-site FFIEC IT Audits.
FYI
- DHS warns against ‘password spray’ brute force attacks - The DHS
recently issued a warning against the use of common and or easily
guessed passwords after several government agencies have been
targeted by “password spray” attacks.
https://www.scmagazine.com/home/security-news/cybercrime/the-dhs-recently-issued-a-warning-against-the-use-of-common-and-or-easily-guessed-passwords-after-several-government-agencies-have-been-targeted-by-password-spray-attacks/
The Strange Journey of an NSA Zero-Day—Into Multiple Enemies' Hands
- The notion of a so-called zero-day vulnerability in software is
supposed to mean, by definition, that it's secret. The term refers
to a hackable flaw in code that the software's maker doesn't know
about but that a hacker does—in some cases offering that hacker a
powerful, stealthy skeleton key into the hearts of millions of
computers.
https://www.wired.com/story/nsa-zero-day-symantec-buckeye-china/
Key to success: Tenants finally get physical keys after suing
landlords for fitting Bluetooth smart-lock to front door - Big Apple
residents weren't too appy with apartment block's high-tech security
system - Updated The owners of a Manhattan apartment block have
agreed to give their tenants mechanical keys to end a court battle
over a keyless smart-lock system.
https://www.theregister.co.uk/2019/05/08/ny_judge_mechanical_key/
Wargaming cannot take the place of real cyber protection - It’s no
big secret: cyberattacks keep business leaders up at night. In a
World Economic Forum executive study in November, cyberattacks were
rated as the fifth biggest risk to businesses worldwide, one place
behind cybercrime and fraud, and the number one business risk in the
U.S.
https://www.scmagazine.com/home/opinion/executive-insight/war-gaming-cannot-take-the-place-of-real-cyber-protection/
Baltimore will not pay ransomware demand: Mayor Young - Newly minted
Baltimore Mayor Bernard Young said the city has no intention of
paying the ransom demand set by the cyberattackers who have locked
up a large portion of the city’s servers with Robbinhood ransomware.
https://www.scmagazine.com/home/security-news/ransomware/baltimore-will-not-pay-ransomware-demand-mayor-young/
Equifax data breach recovery costs pass $1 billion - In Equifax’s
latest Security and Exchange Commission filing the company is
estimating it has spent about $1.4 billion recovering from its 2017
data breach that exposed the PII of 148 million customers, according
to a published report.
https://www.scmagazine.com/home/security-news/data-breach/equifax-data-breach-recovery-costs-pass-1-billion/
Why Rewards for Loyal Spenders Are ‘a Honey Pot for Hackers’ - The
punch cards stuffed in your wallet know next to nothing about you,
except maybe how many frozen yogurts you still need to buy to get a
free one.
https://www.nytimes.com/2019/05/11/business/rewards-loyalty-program-fraud-security.html
Offline and in the dark: Inside the CCH outage - Wolters Kluwer NV
makes the software on which many of the world’s small and midsized
accounting firms run. Early last week, a cyberattack took down that
software and presented a case study in how not to communicate with
customers over a hack.
https://www.accountingtoday.com/articles/a-massive-accounting-hack-kept-clients-offline-and-in-the-dark
IRS extends tax filing deadline following attack on Wolters Kluwer
CCH cloud accounting service - The United States Internal Revenue
Service (IRS) has approved a seven-day extension for filings that
were affected by the downtime last week of Wolters Kluwer’s CCH
accounting service, following the discovery of malware.
https://www.grahamcluley.com/irs-extends-tax-filing-deadline-following-attack-on-wolters-kluwer-cch-cloud-accounting-service/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Wolters Kluwer still down from May 6 cyberattack - The information
services firm Wolters Kluwer has been battling to recover from a
cyberattack that forced the company to shut down many of its tax and
accounting software applications, which is causing issues for those
using the affected products.
https://www.scmagazine.com/home/security-news/malware/wolters-kluwer-still-down-from-may-6-cyberattack/
https://www.theregister.co.uk/2019/05/08/cch_hit_by_malware/
Amazon hackers stole funds from merchant accounts - Hackers stole
funds from approximately Amazon.com Inc. Seller Central merchant
accounts during a six-month period in 2018.
https://www.scmagazine.com/home/security-news/amazon-hackers-stole-funds-from-merchant-accounts/
Hackers hold 275M records on Indian citizens for ransom after
removing them from open database - One week after a researcher
revealed a publicly configured database exposing more than 275
million sensitive records on Indian citizens, a hacking group
removed that data and replaced it with an apparent ransom note.
https://www.scmagazine.com/home/security-news/hackers-hold-275m-records-on-indian-citizens-for-ransom-after-removing-them-from-open-database/
Report: Hackers claim compromise of four AV firms, offer source code
for sale - A high-profile hacking collective claims it compromised
the networks of four premiere U.S. anti-virus vendors, and is
offering to sell their stolen source code for $300,000, according to
researchers.
https://www.scmagazine.com/home/security-news/data-breach/report-hackers-claim-to-compromise-4-av-firms-offer-source-code-for-sale/
Indiana Pacers basketball team falls for phishing attack - The
Indiana Pacers franchise, Pacers Sports & Entertainment (PSE), fell
victim to a phishing attack which resulted in unauthorized gaining
access to emails containing personal information related to a
limited number of individuals.
https://www.scmagazine.com/home/security-news/phishing/the-indiana-pacers-franchise-pacers-sports-entertainment-pse-fell-victim-to-a-phishing-attack/
Anti-virus vendors named in Fxmsp’s alleged source code breach
respond - McAfee, Symantec and Trend Micro are reportedly the
anti-virus companies whose source code the cybercriminal group Fxmsp
claims to have stolen. Comments issued by the vendors minimized the
threat, although Trend Micro did confirm that a breach had occurred.
https://www.scmagazine.com/home/security-news/anti-virus-vendors-named-in-fxmsps-alleged-source-code-breach-respond/
Tweet may contain login credentials taken in Baltimore ransomware
attack - Baltimore’s issues stemming from a May 7 Robbinhood
ransomware attack are not only starting to impact some aspects of
the city’s economy, but the security firm Armor came across a Tweet
that may contain information gleaned from the Baltimore’s network.
https://www.scmagazine.com/home/security-news/ransomware/tweet-may-contain-login-credentials-taken-in-baltimore-ransomware-attack/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
Board and
Management Oversight -
Principle 5: Banks should use transaction authentication methods
that promote non-repudiation and establish accountability for
e-banking transactions.
Non-repudiation involves creating proof of the origin or
delivery of electronic information to protect the sender against
false denial by the recipient that the data has been received, or to
protect the recipient against false denial by the sender that the
data has been sent. Risk of transaction repudiation is already an
issue with conventional transactions such as credit cards or
securities transactions. However, e-banking heightens this risk
because of the difficulties of positively authenticating the
identities and authority of parties initiating transactions, the
potential for altering or hijacking electronic transactions, and the
potential for e-banking users to claim that transactions were
fraudulently altered.
To address these heightened concerns, banks need to make
reasonable efforts, commensurate with the materiality and type of
the e-banking transaction, to ensure that:
1) E-banking systems are designed to reduce the likelihood that
authorized users will initiate unintended transactions and that
customers fully understand the risks associated with any
transactions they initiate.
2) All parties to the transaction are positively authenticated
and control is maintained over the authenticated channel.
3) Financial transaction data are protected from alteration and
any alteration is detectable.
Banking organizations have begun to employ various techniques that
help establish non-repudiation and ensure confidentiality and
integrity of e-banking transactions, such as digital certificates
using public key infrastructure (PKI). A bank may issue a digital
certificate to a customer or counterparty to allow for their unique
identification/authentication and reduce the risk of transaction
repudiation. Although in some countries customers' rights to
disclaim transactions is provided in specific legal provisions,
legislation has been passed in certain national jurisdictions making
digital signatures legally enforceable. Wider global legal
acceptance of such techniques is likely as technology continues to
evolve.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION -
NETWORK ACCESS
Firewall Services and Configuration
Firewalls may provide some additional services:
! Network address translation (NAT) - NAT readdresses outbound
packets to mask the internal IP addresses of the network. Untrusted
networks see a different host IP address from the actual internal
address. NAT allows an institution to hide the topology and address
schemes of its trusted network from untrusted networks.
! Dynamic host configuration protocol (DHCP) - DHCP assigns IP
addresses to machines that will be subject to the security controls
of the firewall.
! Virtual Private Network (VPN) gateways - A VPN gateway provides
an encrypted tunnel between a remote external gateway and the
internal network. Placing VPN capability on the firewall and the
remote gateway protects information from disclosure between the
gateways but not from the gateway to the terminating machines.
Placement on the firewall, however, allows the firewall to inspect
the traffic and perform access control, logging, and malicious code
scanning.
One common firewall implementation in financial institutions
hosting Internet applications is a DMZ, which is a neutral Internet
accessible zone typically separated by two firewalls. One firewall
is between the institution's private network and the DMZ and then
another firewall is between the DMZ and the outside public network.
The DMZ constitutes one logical security domain, the outside public
network is another security domain, and the institution's internal
network may be composed of one or more additional logical security
domains. An adequate and effectively managed firewall can ensure
that an institution's computer systems are not directly accessible
to any on the Internet.
Financial institutions have a variety of firewall options from
which to choose depending on the extent of Internet access and the
complexity of their network. Considerations include the ease of
firewall administration, degree of firewall monitoring support
through automated logging and log analysis, and the capability to
provide alerts for abnormal activity.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.2.2
System Operational Authority/Ownership
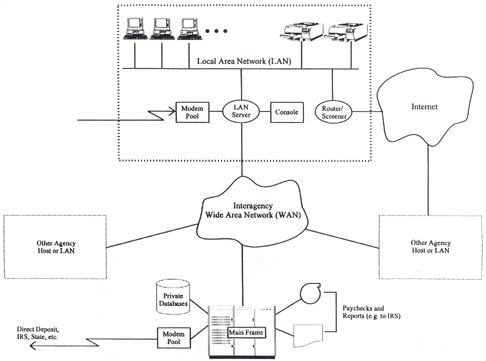
The system components
contained within the large dashed rectangle shown in the figure
below are managed and operated by an organization within HGA known
as the Computer Operations Group (COG). This group includes the PCs,
LAN, server, console, printers, modem pool, and router. The WAN is
owned and operated by a large commercial telecommunications company
that provides WAN services under a government contract. The
mainframe is owned and operated by a federal agency that acts as a
service provider for HGA and other agencies connected to the WAN.
20.2.3 System
Applications
PCs on HGA's LAN are
used for word processing, data manipulation, and other common
applications, including spreadsheet and project management tools.
Many of these tasks are concerned with data that are sensitive with
respect to confidentiality or integrity. Some of these documents and
data also need to be available in a timely manner.
The mainframe also
provides storage and retrieval services for other databases
belonging to individual agencies. For example, several agencies,
including HGA, store their personnel databases on the mainframe;
these databases contain dates of service, leave balances, salary and
W-2 information, and so forth.
In addition to their
time and attendance application, HGA's PCs and the LAN server are
used to manipulate other kinds of information that may be sensitive
with respect to confidentiality or integrity, including
personnel-related correspondence and draft contracting documents.
20.3 Threats
to HGA's Assets
Different assets of HGA
are subject to different kinds of threats. Some threats are
considered less likely than others, and the potential impact of
different threats may vary greatly. The likelihood of threats is
generally difficult to estimate accurately. Both HGA and the risk
assessment's authors have attempted to the extent possible to base
these estimates on historical data, but have also tried to
anticipate new trends stimulated by emerging technologies (e.g.,
external networks).
|