|
FYI
- NIST Updates SP 800-171 to Help Defend Sensitive Information from
Cyberattack - An update to one of the National Institute of
Standards and Technology’s (NIST) information security documents
offers strategies to help protect sensitive information that is
stored in computers supporting critical government programs and high
value assets.
https://www.nist.gov/news-events/news/2019/06/nist-updates-sp-800-171-help-defend-sensitive-information-cyberattack
Riviera Beach, Fla., pays $600,000 ransom payment - The Riviera
Beach City Council voted this week to pay a 65-bitcoin, or $600,000,
ransom in an attempt to have its computer system decrypted following
a May 29 ransomware attack.
https://www.scmagazine.com/home/security-news/ransomware/riviera-beach-fla-pays-600000-ransom-payment/
U.S. launched cyberattacks on Iranian intel targets, report -
President Trump may have pulled back at the 11th hour from
airstrikes on Iranian radar and military targets, but U.S. Cyber
Command did hit cyber targets within the Iranian intelligence
apparatus last week.
https://www.scmagazine.com/home/network-security/u-s-launched-cyberattacks-on-iranian-intel-targets-report/
NASA takes Caltech’s JPL to task over cybersecurity issues - NASA’s
Jet Propulsion Laboratory (JPL) is best known as the home for a
variety of space-faring endeavors, but the facility is also tasked
with defending the space agency from cyberattacks.
https://www.scmagazine.com/home/network-security/nasa-takes-caltechs-jpl-to-task-over-cybersecurity-issues/
Career advice for current and future CISOs - Cybersecurity
professionals have a unique opportunity to make the world a safer
place. Our work protects important economic and public interests
from real threats. It’s a high-stress, high-reward job career path
that can provide life-long satisfaction.
https://www.scmagazine.com/home/opinion/executive-insight/career-advice-for-current-and-future-cisos/
Dell SupportAssist bug leaves millions of PCs vulnerable - A
vulnerability in Dell’s SupportAssist software, a software designed
to protect users from vulnerabilities, has left millions of PCs
vulnerable to remote takeover.
https://www.scmagazine.com/home/security-news/vulnerabilities/a-vulnerability-in-dells-supportassist-software-a-software-designed-to-protect-users-from-vulnerabilities-has-left-millions-of-pcs-vulnerable-to-remote-takeover/
Girls Go CyberStart competition proves NJ high schoolers are leading
the pack in cybersecurity - With so many companies, retailers,
governments and consumers all vulnerable to cyberattacks and data
breaches these days, there’s never been a greater need for
cybersecurity — or the specialists who know how to protect
electronic devices from these potentially devastating threats.
http://www.jerseysbest.com/girls-go-cyberstart-competition-proves-nj-high-schoolers-are-leading-the-pack-in-cybersecurity/
Minnesota Cop Awarded $585K After Colleagues Snooped on Her DMV Data
- In 2013, Amy Krekelberg received an unsettling notice from
Minnesota’s Department of Natural Resources: An employee had abused
his access to a government driver’s license database and snooped on
thousands of people in the state, mostly women.
https://www.wired.com/story/minnesota-police-dmv-database-abuse/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Phishing campaign impersonates email alerts from DHS - An ongoing
email-based phishing scam is attempting to fool recipients into
opening malicious attachments disguised as notifications from the
U.S. Department of Homeland Security (DHS), according to the
Cybersecurity and Infrastructure Security Agency, in a warning
posted on the official US-CERT web site this past Tuesday.
https://www.scmagazine.com/home/security-news/phishing/phishing-campaign-impersonates-email-alerts-from-dhs/
Desjardins, Canada's largest credit union, announces security breach
- Data for 2.9 million bank members was taken from the bank's system
by a now-fired employee.
https://www.zdnet.com/article/desjardins-canadas-largest-credit-union-announces-security-breach/
Insider exposes PII of 2.9 million Desjardins customers - The
Canadian financial institution Desjardins was the victim of an
insider threat resulting in the data of 2.9 million customers being
exposed, including crucial personal and business information.
https://www.scmagazine.com/home/security-news/insider-threats/insider-exposes-pii-of-2-9-million-desjardins-customers/
Sun Prairie, Wis. warns of data breach after intruder accesses
employee email accounts - For nearly two months this year, an
unauthorized party had illegitimate access to the email accounts of
certain employees working for the city of Sun Prairie, Wisconsin.
https://www.scmagazine.com/home/security-news/sun-prairie-wisc-warns-of-data-breach-after-intruder-accesses-employee-email-accounts/
Second Florida city burned by ransomware and pays attackers - Just
two weeks after Lake City, Fla., government officials said their
municipality was in the process recovering from a June 10 ransomware
attack, the city opted to pay a $460,000 ransom.
https://www.scmagazine.com/home/security-news/ransomware/second-florida-city-burned-by-ransomware-and-pays-attackers/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue covering some of the
issues discussed in the "Risk Management Principles for Electronic
Banking" published by the Basel Committee on Bank Supervision.
Board and Management Oversight
- Principle 11: Banks
should ensure that adequate information is provided on their
websites to allow potential customers to make an informed conclusion
about the bank's identity and regulatory status of the bank prior to
entering into e-banking transactions.
To minimize legal and reputational risk associated with e-banking
activities conducted both domestically and cross-border, banks
should ensure that adequate information is provided on their
websites to allow customers to make informed conclusions about the
identity and regulatory status of the bank before they enter into
e-banking transactions.
Examples of such information that a bank could provide on its own
website include:
1) The name of the bank and the location of its head office (and
local offices if applicable).
2) The identity of the primary bank supervisory authority(ies)
responsible for the supervision of the bank's head office.
3) How customers can contact the bank's customer service center
regarding service problems, complaints, suspected misuse of
accounts, etc.
4) How customers can access and use applicable Ombudsman or
consumer complaint schemes.
5) How customers can obtain access to information on applicable
national compensation or deposit insurance coverage and the level of
protection that they afford (or links to websites that provide such
information).
6) Other information that may be appropriate or required by
specific jurisdictions.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY CONTROLS -
IMPLEMENTATION - APPLICATION
ACCESS
(Part
1 of 2)
Sensitive or mission - critical applications should incorporate
appropriate access controls that restrict which application
functions are available to users and other applications. The most
commonly referenced applications from an examination perspective
support the information processing needs of the various business
lines. These computer applications allow authorized users or other
applications to interface with the related database. Effective
application access control can enforce both segregation of duties
and dual control. Access rights to sensitive or critical
applications and their database should ensure that employees or
applications have the minimum level of access required to perform
their business functions. Effective application access control
involves a partnership between the security administrators, the
application programmers (including TSPs and vendors), and the
business owners.
Some security software programs will integrate access control for
the operating system and some applications. That software is useful
when applications do not have their own access controls, and when
the institution wants to rely on the security software instead of
the application's access controls. Examples of such security
software products for mainframe computers include RACF, CA - ACF2,
and CA - TopSecret. Institutions should understand the functionality
and vulnerabilities of their application access control solutions
and consider those issues in their risk assessment process.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.4.1
General Use and Administration of HGA's Computer System
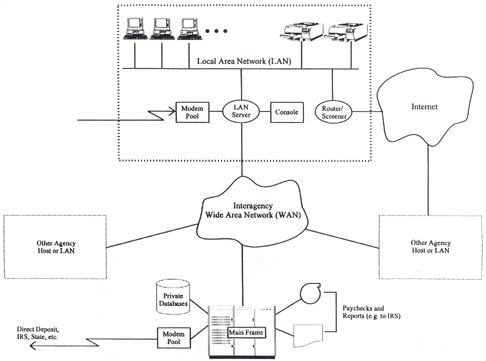
HGA's Computer
Operations Group (COG) is responsible for controlling,
administering, and maintaining the computer resources owned and
operated by HGA. These functions are depicted in Figure below
enclosed in the large, dashed rectangle. Only individuals holding
the job title System Administrator are authorized to establish
log-in ID's and passwords on multiuser HGA systems (e.g., the LAN
server). Only HGA's employees and contract personnel may use the
system, and only after receiving written authorization from the
department supervisor (or, in the case of contractors, the
contracting officer) to whom these individuals report.
COG issues copies of
all relevant security policies and procedures to new users. Before
activating a system account for new users, COG requires that they
(1) attend a security awareness and training course or complete an
interactive computer-aided-instruction training session and (2) sign
an acknowledgment form indicating that they understand their
security responsibilities.
Authorized users are
assigned a secret log-in ID and password, which they must not share
with anyone else. They are expected to comply with all of HGA's
password selection and security procedures (e.g., periodically
changing passwords). Users who fail to do so are subject to a range
of penalties.
Users creating data
that are sensitive with respect to disclosure or modification are
expected to make effective use of the automated access control
mechanisms available on HGA computers to reduce the risk of exposure
to unauthorized individuals. (Appropriate training and education are
in place to help users do this.) In general, access to
disclosure-sensitive information is to be granted only to
individuals whose jobs require it.
|