|
MISCELLANEOUS CYBERSECURITY NEWS:
Bank customers now rank security and fraud protection ahead of low
fees - Financial firms have long understood that security is a high
priority for their customers - albeit typically not as high a
priority as the banking fees they are charged.
https://www.scmagazine.com/analysis/identity-and-access/bank-customers-now-rank-security-and-fraud-protection-ahead-of-low-fees
Security concerns with messaging use cost Wall Street banks over $1B
in fines - Several well-known Wall Street U.S. banks will be dipping
into their own pockets to pay more than $1 billion all together in
regulatory fines because their traders used private messaging
applications such as WhatsApp in their work, due to potential
security and privacy issues of this practice.
https://www.scmagazine.com/analysis/compliance/security-concerns-with-messaging-use-cost-wall-street-banks-over-1b-in-fines
Cyber agency highlights emerging threats from quantum computing -
The Cybersecurity and Infrastructure Security Agency (CISA) released
new advice Wednesday on ways critical infrastructure should prepare
for potential security risks stemming from quantum computing.
https://thehill.com/policy/cybersecurity/3614549-cyber-agency-highlights-emerging-threats-from-quantum-computing/
Ransomware, nation-state attacks top Federal Reserve’s IT security
concerns for banks - The Federal Reserve Board, aka the Fed,
published its annual “Cybersecurity and Financial System Resilience”
report earlier this month. Not surprisingly, ransomware attacks,
nation-state incursions and third-party access topped the list of
potential IT security threats to the U.S. financial industry.
https://www.scmagazine.com/analysis/ransomware/ransomware-nation-state-attacks-top-federal-reserves-it-security-concerns-for-banks
‘Bright spots’ highlighted as feds eye security, collaboration
challenges in health sector - Awareness around healthcare’s
longstanding cybersecurity challenges is at an all-time high, as
federal efforts to secure critical infrastructure work to provide
the sector with needed support and Congress looks for deeper insight
into the state of cybersecurity among care partners.
https://www.scmagazine.com/feature/device-security/bright-spots-highlighted-as-feds-eye-security-collaboration-challenges-in-health-sector
FTC sues data broker Kochava over sale of data tying users to health
clinics - The FTC filed a lawsuit against Kochava over the alleged
sale of geolocation data from “hundreds of millions” of mobile
devices, which could tie users to reproductive health clinics,
addiction recovery facilities, places of worship, and homeless and
domestic violence shelters.
https://www.scmagazine.com/analysis/privacy/ftc-sues-data-broker-kochava-over-sale-of-data-tying-users-to-health-clinics
Health-ISAC shares zero trust implementation guide for healthcare
CISOs - Challenges with adopting a zero trust security model in
healthcare boil down two two key issues: the rapid expansion of IoT
devices and authentication complexities tied to “the roaming nature
of some healthcare workers,” according to a new white paper from the
Health-ISAC.
https://www.scmagazine.com/analysis/zero-trust/health-isac-shares-zero-trust-implementation-guide-for-healthcare-cisos
Cyber-Insurance Firms Limit Payouts, Risk Obsolescence - Businesses
need to re-evaluate their cyber-insurance policies as firms like
Lloyd's of London continue to add restrictions, including excluding
losses related to state-backed cyberattackers.
https://www.darkreading.com/risk/cyber-insurance-firms-limit-payouts-risk-obsolescence
Most top mobile carriers retain geolocation data for two years on
average, FCC findings show - Ten of the top 15 mobile carriers
collect geolocation data and provide no way for consumers to
opt-out, according to information from the telecom companies the
Federal Communications Commission published Thursday.
https://www.cyberscoop.com/fcc-geolocation-data-verizon-t-mobile/
Businesses can expect to pay more for cyber insurance by 2025 - A
report by Fitch Ratings on Wednesday may bode well for cyber
insurers, but businesses and their security organizations can expect
to pay more for cyber insurance in the years ahead.
https://www.scmagazine.com/news/vulnerability-management/businesses-can-expect-to-pay-more-for-cyber-insurance-by-2025
Challenges in implementing vulnerability management - Many
organizations struggle to assess and patch systems fast enough to
stay ahead of threats, spurring investment in more aggressive,
proactive vulnerability management strategies during the last two
years, according to findings in a survey conducted by CRA Business
Intelligence in July.
https://www.scmagazine.com/resource/vulnerability-management/challenges-in-implementing-vulnerability-management
CYBERSECURITY ATTACKS, INTRUSIONS, DATA THEFT &
LOSS:
French hospital hit by $10M ransomware attack, sends patients
elsewhere - The Center Hospitalier Sud Francilien (CHSF), a 1000-bed
hospital located 28km from the center of Paris, suffered a
cyberattack on Sunday, which has resulted in the medical center
referring patients to other establishments and postponing
appointments for surgeries.
https://www.bleepingcomputer.com/news/security/french-hospital-hit-by-10m-ransomware-attack-sends-patients-elsewhere/
Attacker snags account details from streaming service Plex - Users
of popular streaming and media organizing service Plex are waking up
to an unpleasant email this morning saying, in the words of a Reg
reader, "Plex have been hacked and their main site is down as we all
rush to change passwords."
https://www.theregister.com/2022/08/24/data_breach_plex_hack/
Quantum ransomware attack disrupts govt agency in Dominican Republic
- The Dominican Republic's Instituto Agrario Dominicano has suffered
a Quantum ransomware attack that encrypted multiple services and
workstations throughout the government agency.
https://www.bleepingcomputer.com/news/security/quantum-ransomware-attack-disrupts-govt-agency-in-dominican-republic/
LastPass source code, blueprints stolen by intruder - Your passwords
are still safe, biz says - Internal source code and documents have
been stolen from LastPass by a cyber-thief.
https://www.theregister.com/2022/08/25/lastpass_security/
After Kronos fallout, Ascension hospital settles wage dispute
lawsuit for $19.7M - Sacred Heart Health System and Ascension Health
in Florida have reached a $19.7 million settlement with a number of
employees over several wage disputes, some which were tied to the
Kronos outage in December 2021 and the payroll disruptions that
followed.
https://www.scmagazine.com/analysis/ransomware/after-kronos-fallout-ascension-hospital-settles-wage-dispute-lawsuit-for-19-7m
Ransomware-as-a-service group targets more than 75 organizations -
Researchers on Thursday reported that the ransomware-as-a-service (RaaS)
group known as Black Basta has compromised more than 75
organizations over the past several months.
https://www.scmagazine.com/news/cloud-security/ransomware-as-a-service-group-targets-more-than-75-organizations
Okta Says Customer Data Compromised in Twilio Hack - Identity and
access management provider Okta said last week that customer mobile
phone numbers and SMS messages containing one-time passwords (OTPs)
were compromised during the recent Twilio cyberattack.
https://www.securityweek.com/okta-says-customer-data-compromised-twilio-hack
Montenegro says Russian cyberattacks threaten key state functions -
Members of the government in Montenegro are stating that the country
is being hit with sophisticated and persistent cyberattacks that
threaten the country’s essential infrastructure.
https://www.bleepingcomputer.com/news/security/montenegro-says-russian-cyberattacks-threaten-key-state-functions/
134K Common Ground plan members added to vendor’s ransomware fallout
- Common Ground Healthcare Cooperative recently informed 133,714
plan members that their data was likely accessed during a hacking
incident and subsequent ransomware attack of its mailing vendor,
OneTouchPoint.
https://www.scmagazine.com/analysis/ransomware/134k-common-ground-plan-members-added-to-vendors-ransomware-fallout
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
Risk Management of
Outsourced Technology Services
Due Diligence in Selecting a Service Provider
Some of the factors that institutions should consider when
performing due diligence in selecting a service provider are
categorized and listed below. Institutions should review the service
provider’s due diligence process for any of its significant
supporting agents (i.e., subcontractors, support vendors, and other
parties). Depending on the services being outsourced and the level
of in-house expertise, institutions should consider whether to hire
or consult with qualified independent sources. These sources include
consultants, user groups, and trade associations that are familiar
with products and services offered by third parties. Ultimately, the
depth of due diligence will vary depending on the scope and
importance of the outsourced services as well as the risk to the
institution from these services.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
ELECTRONIC AND PAPER - BASED MEDIA HANDLING
DISPOSAL
Financial institutions need appropriate disposal procedures for
both electronic and paper based media. Policies should prohibit
employees from discarding sensitive media along with regular garbage
to avoid accidental disclosure. Many institutions shred paper -
based media on site and others use collection and disposal services
to ensure the media is rendered unreadable and unreconstructable
before disposal. Institutions that contract with third parties
should use care in selecting vendors to ensure adequate employee
background checks, controls, and experience.
Computer - based media presents unique disposal problems.
Residual data frequently remains on media after erasure. Since that
data can be recovered, additional disposal techniques should be
applied to sensitive data. Physical destruction of the media, for
instance by subjecting a compact disk to microwaves, can make the
data unrecoverable. Additionally, data can sometimes be destroyed
after overwriting. Overwriting may be preferred when the media will
be re - used. Institutions should base their disposal policies on
the sensitivity of the information contained on the media and,
through policies, procedures, and training, ensure that the actions
taken to securely dispose of computer-based media adequately protect
the data from the risks of reconstruction. Where practical,
management should log the disposal of sensitive media, especially
computer - based media.
TRANSIT
Financial institutions should maintain the security of media
while in transit or when shared with third parties. Policies should
include:
! Restrictions on the carriers used and procedures to verify the
identity of couriers,
! Requirements for appropriate packaging to protect the media
from damage,
! Use of encryption for transmission of sensitive information,
! Security reviews or independent security reports of receiving
companies, and
! Use of nondisclosure agreements between couriers and third
parties.
Financial institutions should address the security of their back
- up tapes at all times, including when the tapes are in transit
from the data center to off - site storage.
Return to the top of the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.2.2
System Operational Authority/Ownership
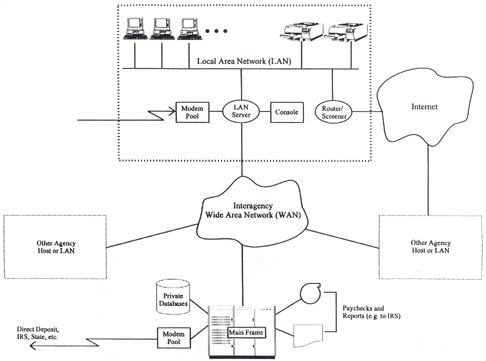
The system components
contained within the large dashed rectangle shown in the figure
below are managed and operated by an organization within HGA known
as the Computer Operations Group (COG). This group includes the PCs,
LAN, server, console, printers, modem pool, and router. The WAN is
owned and operated by a large commercial telecommunications company
that provides WAN services under a government contract. The
mainframe is owned and operated by a federal agency that acts as a
service provider for HGA and other agencies connected to the WAN.
20.2.3 System
Applications
PCs on HGA's LAN are
used for word processing, data manipulation, and other common
applications, including spreadsheet and project management tools.
Many of these tasks are concerned with data that are sensitive with
respect to confidentiality or integrity. Some of these documents and
data also need to be available in a timely manner.
The mainframe also
provides storage and retrieval services for other databases
belonging to individual agencies. For example, several agencies,
including HGA, store their personnel databases on the mainframe;
these databases contain dates of service, leave balances, salary and
W-2 information, and so forth.
In addition to their
time and attendance application, HGA's PCs and the LAN server are
used to manipulate other kinds of information that may be sensitive
with respect to confidentiality or integrity, including
personnel-related correspondence and draft contracting documents.
20.3 Threats
to HGA's Assets
Different assets of HGA
are subject to different kinds of threats. Some threats are
considered less likely than others, and the potential impact of
different threats may vary greatly. The likelihood of threats is
generally difficult to estimate accurately. Both HGA and the risk
assessment's authors have attempted to the extent possible to base
these estimates on historical data, but have also tried to
anticipate new trends stimulated by emerging technologies (e.g.,
external networks).
|