|
MISCELLANEOUS CYBERSECURITY NEWS:
Cybersecurity: 2022 Cybersecurity Resource Guide for Financial
Institutions - The 2022 guide lists voluntary programs and
actionable initiatives that are designed for or are available to
help financial institutions meet their security control objectives
and prepare to respond to cyber incidents.
https://occ.gov/news-issuances/bulletins/2022/bulletin-2022-22.html
The people problem (and solution): Challenging cybersecurity
awareness assumptions - Cybersecurity awareness is at its core about
people. And Cybersecurity Awareness Month - October - is about
educating and training people to be smarter about security.
https://www.scmagazine.com/news/security-awareness/the-people-problem-and-solution-challenging-cybersecurity-awareness-assumptions
FDA bill passes without cybersecurity requirements for medical
devices - The FDA appropriations bill passed this week did not
include previously introduced medical device cybersecurity rules
requiring developers to create processes for identifying and
addressing security vulnerabilities and threats, and to include
software bill of materials.
https://www.scmagazine.com/analysis/device-security/fda-bill-passes-without-cybersecurity-requirements-for-medical-devices
Senate Homeland Approves Fed Software Inventory Bill - The Senate
Homeland Security and Governmental Affairs Committee approved by
voice vote today a bill that would order Federal government agencies
to undertake an inventory of all software used by the government.
https://www.meritalk.com/articles/senate-homeland-approves-fed-software-inventory-bill/
Why human nature often trumps security - Cybersecurity risk is the
top concern for CEOs globally, with elevated risks and awareness
spurring increased investment in network defenses and security
features within systems. But there is one threat executives cannot
program away: humans.
https://www.scmagazine.com/feature/security-awareness/manage-your-expectations-why-human-nature-often-trumps-security
Security leaders should replace the assumption of a breach with a
different approach - For security leaders to earn our seat at the
table, we need to deliver value by solving the right problems and
communicating what counts.
https://www.scmagazine.com/perspective/leadership/security-leaders-should-replace-the-assumption-of-a-breach-with-a-different-approach
Healthcare industry group asks NIST for security guidance for small,
low-resourced providers - The Healthcare & Public Health Sector
Coordinating Council urged the National Institute of Standards and
Technology to provide more resources tailored to lower resourced and
smaller providers, which face unique challenges that require more
support than other healthcare entities and typically struggle to
quickly adopt new standards.
https://www.scmagazine.com/analysis/compliance/healthcare-industry-group-asks-nist-for-security-guidance-for-small-low-resourced-providers
CISOs and board members view cyber risk through different lens -
There is a disconnect between the boardroom and chief information
security officers around the world when evaluating cyber risk.
https://www.scmagazine.com/analysis/security-awareness/cisos-and-board-members-view-cyber-risk-through-different-lens
Should we take comfort in knowing that threat actors are finding
ways to bypass MFA? - Threat actors are starting to find ways to
bypass multi-factor authentication, a sign that some security
researchers say may demonstrate that MFA has become more mainstream,
according to a report released Tuesday by Secureworks.
https://www.scmagazine.com/news/identity-and-access/should-we-take-comfort-in-knowing-that-threat-actors-are-finding-ways-to-bypass-mfa
CYBERSECURITY ATTACKS, INTRUSIONS, DATA THEFT &
LOSS:
Australia asks FBI to help find attacker who stole data from
millions of users - Australian authorities have asked the United
States Federal Bureau of Investigation (FBI) to assist with
investigations into the data breach at local telco Optus.
https://www.theregister.com/2022/09/28/optus_data_breach_summary/
Magellan Health settles for $1.43M after data breach, delayed
notification - Magellan Health has agreed to pay breach victims
$1.43 million to resolve claims its allegedly inadequate security
enabled an undetected phishing attack and subsequent patient data
breach in 2019.
https://www.scmagazine.com/analysis/incident-response/magellan-health-settles-for-1-43m-after-data-breach-delayed-notification
More than 248,000 files leaked on the dark web in LAUSD ransomware
case - That’s how researchers at Check Point on Monday described the
data and documents reportedly released Sunday by the Vice Society
ransomware gang after the Los Angeles Unified School District
refused to pay a ransom following the group’s attack on LAUSD in
September.
https://www.scmagazine.com/analysis/ransomware/more-than-248000-files-leaked-on-the-dark-web-in-lausd-ransomware-case
Optus reveals extent of data breach, but stays mum on how it
happened - Of the 9.8 million customers impacted by the data breach,
1.2 million have at least one form of identification number that is
valid, says the Singtel-owned Australian operator, adding that it
has brought in Deloitte to investigate the breach, including how it
occurred.
https://www.zdnet.com/article/optus-reveals-extent-of-data-breach-but-stays-mum-on-how-it-happened/
Lazarus hackers abuse Dell driver bug using new FudModule rootkit -
The notorious North Korean hacking group 'Lazarus' was seen
installing a Windows rootkit that abuses a Dell hardware driver in a
Bring Your Own Vulnerable Driver attack.
https://www.bleepingcomputer.com/news/security/lazarus-hackers-abuse-dell-driver-bug-using-new-fudmodule-rootkit/
CommonSpirit cyberattack spurs IT outages at CHI Memorial, hospitals
across US - A cyberattack deployed against CommonSpirit has led to
IT outages at hospitals across the U.S., including multiple CHI
Memorial hospitals in Chattanooga, Tennessee.
https://www.scmagazine.com/analysis/ransomware/commonspirit-cyberattack-spurs-it-outages-at-chi-memorial-hospitals-across-us
Family Medical informs 234K patients of possible data compromise -
Family Medical Center Services recently informed 233,948 patients
that their data was potentially compromised after a “network data
security incident” on July 26.
https://www.scmagazine.com/analysis/ransomware/family-medical-reports-informs-234k-patients-of-possible-data-compromise
Ex-Uber chief security officer convicted of covering up 2016 breach
- The former chief security officer for Uber, was convicted
Wednesday of paying hackers $100,000 after they breached the
ride-sharing company in 2016 as if it was a bug bounty rather than
an extortion demand.
https://www.scmagazine.com/news/compliance/ex-uber-chief-security-officer-convicted-of-covering-up-2016-breach
More than 248,000 files leaked on the dark web in LAUSD ransomware
case - Massive. That’s how researchers at Check Point on Monday
described the data and documents reportedly released Sunday by the
Vice Society ransomware gang after the Los Angeles Unified School
District refused to pay a ransom following the group’s attack on
LAUSD in September.
https://www.scmagazine.com/analysis/ransomware/more-than-248000-files-leaked-on-the-dark-web-in-lausd-ransomware-case
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
Risk Management of
Outsourced Technology Services
Due Diligence in Selecting a Service Provider - Contract Issues
Audit
The institution should generally include in the contract the types
of audit reports the institution is entitled to receive (e.g.,
financial, internal control and security reviews). The contract can
specify audit frequency, cost to the institution associated with the
audits if any, as well as the rights of the institution and its
agencies to obtain the results of the audits in a timely manner. The
contract may also specify rights to obtain documentation regarding
the resolution of audit
disclosed deficiencies and inspect the processing facilities and
operating practices of the service provider. Management should
consider, based upon the risk assessment phase, the degree to which
independent internal audits completed by service provider audit
staff can be used and the need for external audits and reviews
(e.g., SAS 70 Type I and II reviews). (AICPA Statement of Auditing
Standards 70 “Reports of Processing of Transactions by Service
Organizations,” known as SAS 70 Reports, are one commonly used form
of external review. Type I SAS 70 reports review the service
provider’s policies and procedures. Type II SAS 70 reports provide
tests of actual controls against policies and procedures.)
For services involving access to open networks, such as
Internet-related services, special attention should be paid to
security. The institution may wish to include contract terms
requiring periodic audits to be performed by an independent party
with sufficient expertise. These audits may include penetration
testing, intrusion detection, and firewall configuration. The
institution should receive sufficiently detailed reports on the
findings of these ongoing audits to adequately assess security
without compromising the service provider’s security. It can be
beneficial to both the service provider and the institution to
contract for such ongoing tests on a coordinated basis given the
number of institutions that may contract with the service provider
and the importance of the test results to the institution.
Reports
Contractual terms should discuss the frequency and type of reports
the institution will receive (e.g., performance reports, control
audits, financial statements, security, and business resumption
testing reports). Guidelines and fees for obtaining custom reports
should also be discussed.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
INTRUSION DETECTION AND RESPONSE
A maxim of security is "prevention is ideal, but detection is a
must." Security systems must both restrict access and protect
against the failure of those access restrictions. When those systems
fail, however, an intrusion occurs and the only remaining protection
is a detection - and - response capability. The earlier an intrusion
is detected, the greater the institution's ability to mitigate the
risk posed by the intrusion. Financial institutions should have a
capability to detect and react to an intrusion into their
information systems.
INTRUSION DETECTION
Preparation for intrusion detection generally involves
identifying data flows to monitor for clues to an intrusion,
deciding on the scope and nature of monitoring, implementing that
monitoring, and establishing a process to analyze and maintain
custody over the resulting information. Additionally, legal
requirements may include notifications of users regarding the
monitoring and the extent to which monitoring must be performed as
an ordinary part of ongoing operations.
Adequate preparation is a key prerequisite to detection. The
best intrusion detection systems will not identify an intrusion if
they are not located to collect the relevant data, do not analyze
correct data, or are not configured properly. Even if they detect an
intrusion, the information gathered may not be usable by law
enforcement if proper notification of monitoring and preservation of
data integrity has not taken place.
Return to the top of the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)20.4.1
General Use and Administration of HGA's Computer System
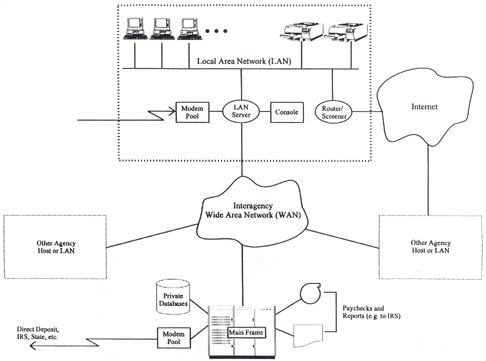
HGA's Computer
Operations Group (COG) is responsible for controlling,
administering, and maintaining the computer resources owned and
operated by HGA. These functions are depicted in Figure below
enclosed in the large, dashed rectangle. Only individuals holding
the job title System Administrator are authorized to establish
log-in ID's and passwords on multiuser HGA systems (e.g., the LAN
server). Only HGA's employees and contract personnel may use the
system, and only after receiving written authorization from the
department supervisor (or, in the case of contractors, the
contracting officer) to whom these individuals report.
COG issues copies of
all relevant security policies and procedures to new users. Before
activating a system account for new users, COG requires that they
(1) attend a security awareness and training course or complete an
interactive computer-aided-instruction training session and (2) sign
an acknowledgment form indicating that they understand their
security responsibilities.
Authorized users are
assigned a secret log-in ID and password, which they must not share
with anyone else. They are expected to comply with all of HGA's
password selection and security procedures (e.g., periodically
changing passwords). Users who fail to do so are subject to a range
of penalties.
Users creating data
that are sensitive with respect to disclosure or modification are
expected to make effective use of the automated access control
mechanisms available on HGA computers to reduce the risk of exposure
to unauthorized individuals. (Appropriate training and education are
in place to help users do this.) In general, access to
disclosure-sensitive information is to be granted only to
individuals whose jobs require it.
|