|
Does Your Financial Institution need an
affordable cybersecurity Internet security audit? Yennik, Inc.
has clients in 42 states that rely on our cybersecurity penetration testing audits
to ensure proper Internet security settings and
to
meet the independent diagnostic test requirements of
FDIC, OCC, FRB, and NCUA, which provides compliance with
Gramm-Leach Bliley Act 501(b).
The penetration audit and Internet security testing
is an affordable-sophisticated process than goes far beyond the
simple scanning of ports. The audit
focuses on
a hacker's perspective, which will help
you identify real-world weaknesses.
For more information, give R. Kinney Williams a call today at
806-798-7119 or visit
http://www.internetbankingaudits.com/. |
|
FYI
- Federal Reserve Bank of New York creates cybersecurity team - The
Federal Reserve Bank of New York has formed a team dedicated to
strengthening the bank's “overall supervisory approach to
cybersecurity,” according to a speech given by the bank's top
regulator.
http://www.scmagazine.com/sarah-dahlgren-gives-speech-on-cybersecurity/article/405690/
FYI
- Premera warned to fix security holes shortly before being breached
- Premera Blue Cross was warned to fix security holes weeks before
it was breached.
http://www.scmagazine.com/auditors-told-premera-to-address-vulnerabilities-prior-to-breach/article/404492/
FYI
- State Department Unclassified Network Back Up After Four Days -
The State Department said Tuesday it has reopened Internet service
on its unclassified worldwide email network after it was shut down
for four days to clean up malware and boost defenses against
cyberattacks believed to have started last fall.
http://www.nbcnews.com/news/us-news/state-department-unclassified-network-back-after-four-days-x-n325221
FYI
- FBI’s Plan to Expand Hacking Power Advances Despite Privacy Fears
- A judicial advisory panel Monday quietly approved a rule change
that will broaden the FBI's hacking authority despite fears raised
by Google that the amended language represents a "monumental"
constitutional concern.
http://www.nextgov.com/cybersecurity/2015/03/fbis-plan-expand-hacking-power-advances-despite-privacy-fears/107685/
FYI
- D-Link patches yet more vulns - Consumers rise up to ignore
firmware update en masse - D-Link is moving to patch a bunch of
vulnerabilities in consumer products, which almost certainly means
that most users either won't know the patch is happening or won't
run the update.
http://www.theregister.co.uk/2015/03/18/dlink_patches_yet_more_vulns/
FYI
- Court rules New York sheriff's office must turn over 'stingray'
docs to NYCLU - “Stingray” surveillance device watchdogs won a major
victory on Tuesday when a New York court ordered the Erie County
Sheriff's Office to turn over documents about its purchase and use
of the surveillance devices to the New York Civil Liberties Union (NYCLU).
http://www.scmagazine.com/nyclu-wins-court-case-for-stingray-documents/article/404287/
FYI
- White House names former Facebook exec as first IT director - The
White House has nabbed former Facebook executive David Recordon to
serve as the first-ever director of White House information
technology.
http://www.scmagazine.com/facebooks-recordon-becomes-first-white-house-it-director/article/404589/
FYI
- When DDoS Isn't All About Massive Disruption - New data shows
prevalence of often-undetectable DDoS attacks aimed at quietly
wreaking havoc on the network while performing data exfiltration and
other attacks.
http://www.darkreading.com/perimeter/when-ddos-isnt-all-about-massive-disruption/d/d-id/1319581
FYI
- Ex-tutor in Corona del Mar grade-changing scheme charged with 16
additional felonies - A former tutor suspected of being at the
center of a grade-changing scandal at Corona del Mar High School
will face more than a dozen additional felony charges for accessing
school computers, prosecutors announced Friday.
http://www.ocregister.com/articles/lai-654957-felony-school.html
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Health Insurance Provider Premera Discloses Data Breach - 2015 has
become the year of the health care data breach. A newly disclosed
breach at Premera is reported to have affected up to 11 million
people.
http://www.eweek.com/security/health-insurance-provider-premera-discloses-data-breach.html
FYI
- Rogers victimized by ransomware -A misstep by an IT employee of
Canadian communications conglomerate Rogers Communications allowed
the contractual information of 50-70 of the company's business
customers to be exposed via Twitter.
http://www.scmagazine.com/rogers-victimized-by-ransomware/article/403042/
FYI
- St. Mary's Health breach affects thousands - Indiana-based St.
Mary's Health announced that several employees had their usernames
and passwords compromised, and their email accounts contained
personal information on roughly 4,400 individuals.
http://www.scmagazine.com/st-marys-health-breach-affects-thousands/article/404720/
FYI
- Hilton Honors Flaw Exposed All Accounts - Hospitality giant Hilton
Hotels & Resorts recently started offering Hilton HHonors Awards
members 1,000 free awards points to those who agreed to change their
passwords for the online service prior to April 1, 2015, when the
company said the change would become mandatory.
http://krebsonsecurity.com/2015/03/hilton-honors-flaw-exposed-all-accounts/
FYI
- Hackers Attack GreatFire.org, a Workaround for Websites Censored
in China - For years, a group of anonymous activists known as
GreatFire.org has monitored online censorship in China. This week,
unidentified hackers have tried to put an end to those activists’
efforts with an unprecedented attack.
http://sinosphere.blogs.nytimes.com/2015/03/20/hackers-attack-greatfire-org-a-workaround-for-websites-censored-in-china/?_r=0
FYI
- Israel allegedly spied on U.S. communications for Iranian deal
details - Israel allegedly conducted an espionage campaign on the
U.S. to learn the details of President Obama's possible deal to curb
Iran's nuclear program.
http://www.scmagazine.com/israel-launch-espionage-campaign-against-us/article/405184/
FYI
- Twitch resets passwords following possible breach - Video game
streaming platform Twitch – which is owned by Amazon – announced on
Monday that unauthorized access may have been gained to some user
account information.
http://www.scmagazine.com/twitch-resets-passwords-following-possible-breach/article/405175/
FYI
- NYPD union website hacked - The New York Police Department's
(NYPD) Captains Endowment Association website was hit by a cyber
attack this weekend according to The New York Daily News.
http://www.scmagazine.com/nypd-union-website-hacked/article/404956/
FYI
- Indiana State Medical Association hard drives stolen, nearly 40K
impacted - Indiana State Medical Association (ISMA) is notifying
nearly 40,000 individuals that two archive backup hard drives
containing ISMA group health and life insurance databases were
stolen while being transported to an offsite storage facility.
http://www.scmagazine.com/indiana-state-medical-association-hard-drives-stolen-nearly-40k-impacted/article/405694/
Return to the top of the newsletter
WEB SITE COMPLIANCE - We
continue the series regarding FDIC Supervisory Insights regarding
Incident
Response Programs. (9 of 12)
Organize a public relations program.
Whether a bank is a local, national, or global firm,
negative publicity about a security compromise is a distinct
possibility. To address potential reputation risks associated with a
given incident, some banks have organized public relations programs
and designated specific points of contact to oversee the program. A
well-defined public relations program can provide a specific avenue
for open communications with both the media and the institution's
customers.
Recovery
Recovering from an incident essentially involves restoring systems
to a known good state or returning processes and procedures to a
functional state. Some banks have incorporated the following best
practices related to the recovery process in their IRPs.
Determine whether configurations or processes should be changed.
If an institution is the subject of a security compromise,
the goals in the recovery process are to eliminate the cause of the
incident and ensure that the possibility of a repeat event is
minimized. A key component of this process is determining whether
system configurations or other processes should be changed. In the
case of technical compromises, such as a successful network
intrusion, the IRP can prompt management to update or modify system
configurations to help prevent further incidents. Part of this
process may include implementing an effective, ongoing patch
management program, which can reduce exposure to identified
technical vulnerabilities. In terms of non-technical compromises,
the IRP can direct management to review operational procedures or
processes and implement changes designed to prevent a repeat
incident.
Return to the top of
the newsletter
FFIEC IT SECURITY - We continue our series on the FFIEC
interagency Information Security Booklet.
SECURITY TESTING - OUTSOURCED SYSTEMS
Management is responsible for ensuring institution and customer data
is protected, even when that data is transmitted, processed, or
stored by a service provider. Service providers should have
appropriate security testing based on the risk to their
organization, their customer institutions, and the institution's
customers. Accordingly, management and auditors evaluating TSPs
providers should use the above testing guidance in performing
initial due diligence, constructing contracts, and exercising
ongoing oversight or audit responsibilities. Where indicated by the
institution's risk assessment, management is responsible for
monitoring the testing performed at the service provider through
review of timely audits and test results or other equivalent
evaluations.
Return to the top of the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We continue the series on the
National Institute of Standards and Technology (NIST) Handbook.
Chapter 20 - ASSESSING
AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM (HGA)
20.2
HGA's Computer System
HGA relies
on the distributed computer systems and networks shown in Figure
20.1. They consist of a collection of components, some of which are
systems in their own right. Some belong to HGA, but others are owned
and operated by other organizations. This section describes these
components, their role in the overall distributed system
architecture, and how they are used by HGA.
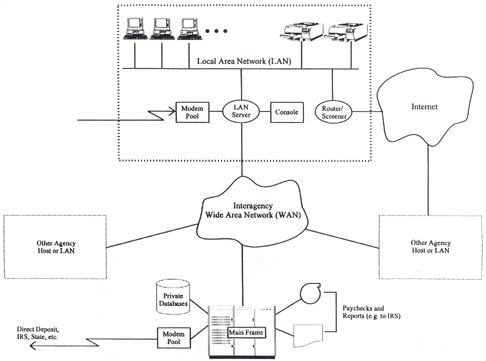
Figure 20.1
|
