|
FYI
- GAO - FDIC Implemented Many Controls over Financial Systems, but
Opportunities for Improvement Remain.
http://www.gao.gov/products/GAO-15-426
FYI
- CIOs Think Many IT Reform Reporting Requirements are Useless -
Agency chief information officers say they’re spending millions of
dollars each year to document their progress meeting the Obama
administration’s IT reform efforts, according to a new Government
Accountability Office report.
http://www.nextgov.com/cio-briefing/2015/04/survey-cios-say-many-it-reform-reporting-requirements-just-busywork/109156/
http://www.gao.gov/assets/670/669434.pdf
FYI
- GAO - Areas for Improvement in the Federal Reserve Banks'
Information Systems Controls.
http://www.gao.gov/products/GAO-15-413R
FYI
- Switch to new chip card stirs up e-payments industry - Starting in
October, switch to new card regulations could usher in greater
acceptance of Apple Pay and its competitors - A behind-the-scenes
switch in the payments industry coming in October will change the
way U.S. consumers shop and could bring wider acceptance for Apple
Pay and its competitors.
http://www.computerworld.com/article/2905715/switch-to-new-chip-card-stirs-up-e-payments-industry.html
FYI
- China suspends rollout of controversial cyber rules - China will
suspend the rollout of new rules restricting Chinese banks’ use of
foreign information technology.
http://thehill.com/policy/cybersecurity/237380-china-suspends-portion-of-controversial-cyber-rules
FYI
- Obama Declares Cyberattacks a 'National Emergency' - President
Obama on Wednesday signed an executive order expanding his
administration's ability to respond to malicious cyberattacks by
allowing financial penalties to be inflicted on foreign actors who
engage in such behavior.
http://www.nextgov.com/cybersecurity/2015/04/obama-declares-cyberattacks-national-emergency/109003/
FYI
- 36 percent in survey don't think its necessary to back up data -
Globally, 36 percent of users don't think it's necessary to back up
their data, a survey from Avast has revealed.
http://www.scmagazine.com/global-survey-says-most-people-dont-back-up-devices/article/407344/
FYI
- HITRUST to sponsor study on healthcare breaches - The Health
Information Trust (HITRUST) Alliance will sponsor a study to analyze
the effects of cyber attacks on healthcare organizations.
http://www.scmagazine.com/hitrust-to-study-healthcare-cyber-attacks/article/407556/
FYI
- Virginia passes digital identity law - Virginia has passed an
electronic identity management law which will usher in standards for
verifying individuals' identities during digital or online
transactions.
http://www.scmagazine.com/virginia-passes-digital-identity-law/article/407548/
FYI
- Tech companies leery of sharing cyber threats with feds - U.S.
tech companies still don't trust the federal government enough to
share information about cyber threats, the top cybersecurity
official at the Department of Homeland Security said Thursday.
http://www.usatoday.com/story/news/politics/2015/04/02/phyllis-schneck-cybersecurity-technology-summit/70838226/
FYI
- Head of Turkey's power grid quits after blackout errors -Minister
- The head of Turkey's state-run power grid has resigned, taking
responsibility for a huge blackout last week likely to have been
caused by management errors, Energy Minister Taner Yildiz said on
Monday.
http://www.reuters.com/article/2015/04/06/turkey-power-outage-idUSL6N0X30GS20150406
FYI
- FCC fines AT&T $25M for call center breaches - The Federal
Communications Commission asserted its information privacy authority
Wednesday by reaching a settlement with AT&T - over data breaches at
a trio of call centers - that includes a $25 million fine.
http://www.scmagazine.com/att-fined-by-fcc-for-breaches-in-three-call-centers/article/408114/
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
-
Locker
combinations accessed in Maryland middle school breach - An
investigation is ongoing by IT professionals into how Westland
Middle School students in Maryland were able to access and make
copies of a list containing information on 1,400 lockers in the
school, including names, locker numbers and locker combinations.
http://www.scmagazine.com/locker-combinations-accessed-in-maryland-middle-school-breach/article/407323/
FYI
-
Fake Pirate
Bay site pushes Nuclear Exploit Kit, distributes trojans - Visitors
to compromised WordPress site were redirected to a fake Pirate Bay
website which is distributing malware as part of a drive-by download
attack.
http://www.scmagazine.com/attackers-target-wordpress-to-distribute-malware/article/407122/
FYI
-
Massachusetts police department pays $500 following ransomware
infection - In Massachusetts, the town of Tewksbury paid a $500
Bitcoin ransom after the police department's network was infected
with a newer variant of CryptoLocker ransomware, according to a
Saturday report by the Tewksbury Town Crier.
http://www.scmagazine.com/massachusetts-police-department-pays-500-following-ransomware-infection/article/407584/
FYI
-
Data
possibly exposed for more than 364K Auburn University students -
Auburn University is notifying more than 364,000 current, former and
prospective students – as well as applicants who never enrolled in
or attended the university – that their personal information was
inadvertently accessible via the internet.
http://www.scmagazine.com/data-possibly-exposed-for-more-than-364k-auburn-university-students/article/407553/
FYI
-
FAA
Computer Systems Hit by Cyberattack Earlier this Year - Hackers
earlier this year attacked a Federal Aviation Administration network
with malicious software, agency officials said Monday.
http://www.nextgov.com/cybersecurity/2015/04/faa-computer-systems-hit-cyberattack-earlier-year/109384/
http://www.scmagazine.com/federal-aviation-administration-falls-victim-to-cyber-attack/article/407774/
FYI
-
Russian
hackers eyed in attack on White House, State Dept. - Russian hackers
that breached a non-classified email system at the State Department,
then dallied around in the agency's network for months, used that
vantage point to gain entry into some areas of the White House
computer system, CNN reported Tuesday.
http://www.scmagazine.com/attackers-positioned-in-state-dept-gained-entry-to-white-house/article/407871/
http://www.cnet.com/news/hackers-who-breached-white-house-network-allegedly-accessed-sensitive-data/
FYI
-
Change.org
bug exposes user email addresses - A vulnerability on the Change.org
website exposed the email addresses "a small subset” of the online
petition organization's users, according to a statement by the
organization's vice president of engineering.
http://www.scmagazine.com/changeorg-bug-exposes-user-email-addresses/article/407643/
FYI
-
NY sheriff
records reveal persistent stingray use without court orders - A New
York court recently ruled that the Erie County Sheriff's Office
should hand over records on stingray use to a privacy rights group –
and documents reveal that, on numerous occasions in recent years,
the surveillance devices were used without obtaining a court order.
http://www.scmagazine.com/ny-sheriff-records-reveal-persistent-stingray-use-without-court-orders/article/408034/
FYI
-
UC
Riverside computer stolen, contained data on about 8,000 students -
The University of California, Riverside (UC Riverside) is notifying
about 8,000 current and former graduate students, graduate
applicants and other related individuals that their personal
information was on a desktop computer that was stolen during a
break-in.
http://www.scmagazine.com/uc-riverside-computer-stolen-contained-data-on-about-8000-students/article/408010/
FYI
-
White
Lodging announces 10 hotels affected in POS breach - Hotel
management company White Lodging said Wednesday that 10 of its
properties have been affected by a data breach that stretched from
July 2014 to February 2015, according to a release.
http://www.scmagazine.com/white-lodging-pos-date-breach-affects-10-properties/article/408298/
FYI
-
At least
750 ambulance patients at risk after Philadelphia FD breach -
Billing information from at least 750 ambulance patients may be at
risk after a breach, the Philadelphia Fire Department said.
http://www.scmagazine.com/philadelphia-fd-data-stolen-potentially-exposing-750-ambulance-patients/article/408031/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
We continue the series
regarding FDIC Supervisory Insights regarding
Incident Response
Programs. (11 of 12)
Last week's best
practices focused on the more common criteria that have been noted
in actual IRPs, but some banks have developed other effective
incident response practices. Examples of these additional practices
are listed below. Organizations may want to review these practices
and determine if any would add value to their IRPs given their
operating environments.
Additional IRP Best Practices
1) Test the incident response plan (via walkthrough or tabletop
exercises) to assess thoroughness.
2) Implement notices on login screens for customer information
systems to establish a basis for disciplinary or legal action.
3) Develop an incident grading system that quantifies the severity
of the incident, helps determine if the incident response plan needs
to be activated, and specifies the extent of notification
escalation.
4) Provide periodic staff awareness training on recognizing
potential indicators of unauthorized activity and reporting the
incident through proper channels. Some institutions have established
phone numbers and e-mail distribution lists for reporting possible
incidents.
5) Inform users about the status of any compromised system they may
be using.
6) Establish a list of possible consultants, in case the bank does
not have the expertise to handle or investigate the specific
incident (especially regarding technical compromises).
7) Establish evidence-gathering and handling procedures aimed at
preserving evidence of the incident and aiding in prosecution
activities.
Return to
the top of the newsletter
FFIEC IT SECURITY -
We continue our series on the FFIEC
interagency Information Security Booklet.
MONITORING AND UPDATING
- MONITORING
Effective monitoring of threats includes both non - technical and
technical sources. Nontechnical sources include organizational
changes, business process changes, new business locations, increased
sensitivity of information, or new products and services. Technical
sources include new systems, new service providers, and increased
access. Security personnel and financial institution management must
remain alert to emerging threats and vulnerabilities. This effort
could include the following security activities:
! Senior management support for strong security policy awareness and
compliance. Management and employees must remain alert to
operational changes that could affect security and actively
communicate issues with security personnel. Business line managers
must have responsibility and accountability for maintaining the
security of their personnel, systems, facilities, and information.
! Security personnel should monitor the information technology
environment and review performance reports to identify trends, new
threats, or control deficiencies. Specific activities could include
reviewing security and activity logs, investigating operational
anomalies, and routinely reviewing system and application access
levels.
! Security personnel and system owners should monitor external
sources for new technical and nontechnical vulnerabilities and
develop appropriate mitigation solutions to address them. Examples
include many controls discussed elsewhere in this booklet including:
- Establishing an effective configuration management
process that monitors for vulnerabilities in hardware and software
and establishes a process to install and test security patches,
- Maintaining up - to - date anti - virus definitions and
intrusion detection attack definitions, and
- Providing effective oversight of service providers and vendors
to identify and react to new security issues.
! Senior management should require periodic security
self-assessments and audits to provide an ongoing assessment of
policy compliance and ensure prompt corrective action of significant
deficiencies.
! Security personnel should have access to automated tools
appropriate for the complexity of the financial institution systems.
Automated security policy and security log analysis tools can
significantly increase the effectiveness and productivity of
security personnel.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)
20.2.2
System Operational Authority/Ownership
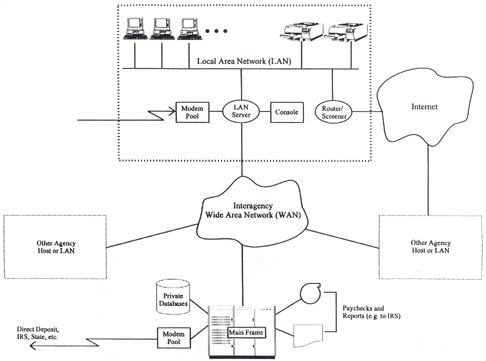
The system components
contained within the large dashed rectangle shown in the figure
below are managed and operated by an organization within HGA known
as the Computer Operations Group (COG). This group includes the PCs,
LAN, server, console, printers, modem pool, and router. The WAN is
owned and operated by a large commercial telecommunications company
that provides WAN services under a government contract. The
mainframe is owned and operated by a federal agency that acts as a
service provider for HGA and other agencies connected to the WAN.
20.2.3 System
Applications
PCs on HGA's LAN are
used for word processing, data manipulation, and other common
applications, including spreadsheet and project management tools.
Many of these tasks are concerned with data that are sensitive with
respect to confidentiality or integrity. Some of these documents and
data also need to be available in a timely manner.
The mainframe also
provides storage and retrieval services for other databases
belonging to individual agencies. For example, several agencies,
including HGA, store their personnel databases on the mainframe;
these databases contain dates of service, leave balances, salary and
W-2 information, and so forth.
In addition to their
time and attendance application, HGA's PCs and the LAN server are
used to manipulate other kinds of information that may be sensitive
with respect to confidentiality or integrity, including
personnel-related correspondence and draft contracting documents.
20.3 Threats
to HGA's Assets
Different assets of HGA
are subject to different kinds of threats. Some threats are
considered less likely than others, and the potential impact of
different threats may vary greatly. The likelihood of threats is
generally difficult to estimate accurately. Both HGA and the risk
assessment's authors have attempted to the extent possible to base
these estimates on historical data, but have also tried to
anticipate new trends stimulated by emerging technologies (e.g.,
external networks).
|
