|
FYI
- Feds Warn Airlines to Look Out for Passengers Hacking Jets - In
response to reports last week that passenger Wi-Fi networks make
some planes vulnerable to hacking, the FBI and TSA have issued an
alert to airlines advising them to be on the lookout for evidence of
tampering or network intrusions.
http://www.wired.com/2015/04/fbi-tsa-warn-airlines-tampering-onboard-wifi/
http://www.scmagazine.com/fbi-issues-flight-hacking-warning/article/410570/
FYI
- Fukushima nuke plant owner told to upgrade from Windows XP - The
Tokyo Electric Power Company (TEPCO), operator of the stricken
Fukushima Daiichi nuclear energy complex, has been told to migrate
48,000 internet-connected PCs off Windows XP sooner rather than
later.
http://www.theregister.co.uk/2015/04/23/fukushima_nuke_plant_owner_told_to_upgrade_from_windows_xp/
FYI
- U.S. plans a cybersecurity center in Silicon Valley - Facility
would promote greater collaboration between the government and
private sector - The U.S. government plans to open a cybersecurity
office in Silicon Valley as part of its push to encourage closer
cooperation between federal law enforcement agencies and the private
sector.
http://www.computerworld.com/article/2912468/cybercrime-hacking/us-plans-a-cybersecurity-center-in-silicon-valley.html
FYI
- Agencies Often Lack Strong Authentication and it’s a Big Problem -
The cyberbullies of the world like to beat up on the U.S.
government. The Office of Management and Budget’s annual Federal
Information Security Management Act report to Congress revealed that
agencies reported nearly 70,000 cyberincidents in fiscal 2014, a 15
percent bump up from the previous year.
http://www.nextgov.com/emerging-tech/emerging-tech-blog/2015/04/agencies-often-lack-strong-authentication-and-its-big-problem/111076/
NCUA Hosting Cybersecurity Webinar - Learn More about
Cyber-Threats and Taking Precautions at Credit Unions - Credit
unions can get up-to-date information on cybersecurity and deterring
cybercrime on a webinar hosted by the National Credit Union
Administration on Wednesday, May 20. The webinar, “Cybersecurity
Basics,” will begin at 2 p.m.
www.ncua.gov/News/Pages/NW20150429CybersecurityWebinar.aspx
ATTACKS, INTRUSIONS, DATA THEFT & LOSS
FYI
- Potential breach brews at Costa Coffee Club - It's not just
caffeine that may make Costa Coffee Club customers eschew coffee for
another beverage - the coffee company has warned its customers that
a possible data breach may have put their information at risk and
has reset passwords for all the club accounts.
http://www.scmagazine.com/costa-coffee-takes-steps-to-thwart-breach/article/411394/
FYI
- About 25K people impacted in Saint Agnes Health Care breach -
Maryland-based Saint Agnes Health Care is notifying approximately
25,000 individuals that their personal information was compromised
by attackers who used a phishing email to gain access to an
employee's email account, which contained the data.
http://www.scmagazine.com/about-25k-people-impacted-in-saint-agnes-health-care-breach/article/411636/
FYI
- Hackers steal nearly $5M from Ryanair's accounts - Amid all the
warnings that cyber attackers will eventually hack commercial
airlines, hijacking and compromising planes and causing other dire
results, hackers staged a more traditional assault on Ryanair,
stealing nearly $5 million from the budget airline's business bank
account.
http://www.scmagazine.com/hackers-steal-nearly-5m-from-ryanairs-accounts/article/412150/
FYI
- FBI investigating Rutgers University in DDoS attack - The FBI is
working with Rutgers University to identify the source of a series
of distributed denial-of-service (DDoS) attacks that have plagued
the school this week.
http://www.scmagazine.com/the-fbi-is-helpign-rutger-inveigate-a-series-of-ddos-attack/article/
FYI
- iPad app glitch delays 74 flights for American Airlines - A glitch
in an iPad navigation application used by pilots caused 74 flight
delays at American Airlines. The issue, which occurred on Tuesday
and Wednesday, was resolved by Wednesday afternoon.
http://www.scmagazine.com/glitch-in-ipad-application-causes-74-flights-delays/article/412040/
FYI
- Texas-based Seton Family of Hospitals notifies 39K patients of
breach - Texas-based Seton Family of Hospitals is notifying
approximately 39,000 patients that an employee's email address –
which contained personal information – was compromised in a phishing
attack.
http://www.scmagazine.com/texas-based-seton-family-of-hospitals-notifies-39k-patients-of-breach/article/412138/
Return to the top
of the newsletter
WEB SITE COMPLIANCE -
OCC - Threats from
Fraudulent Bank Web Sites - Risk Mitigation and Response Guidance
for Web Site Spoofing Incidents (Part 2 of 5)
PROCEDURES TO ADDRESS SPOOFING - Detection
Banks can improve their ability to detect spoofing by monitoring
appropriate information available inside the bank and by searching
the Internet for illegal or unauthorized use of bank names and
trademarks. The following is a list of possible indicators of
Web-site spoofing:
* E-mail messages returned to bank mail servers that were not
originally sent by the bank. In some cases, these e-mails may
contain links to spoofed Web sites;
* Reviews of Web-server logs can reveal links to suspect Web
addresses indicating that the bank's Web site is being copied or
that other malicious activity is taking place;
* An increase in customer calls to call centers or other bank
personnel, or direct communications from consumer reporting spoofing
activity.
Banks can also detect spoofing by searching the Internet for
identifiers associated with the bank such as the name of a company
or bank. Banks can use available search engines and other tools to
monitor Web sites, bulletin boards, news reports, chat rooms,
newsgroups, and other forums to identify usage of a specific company
or bank name. The searches may uncover recent registrations of
domain names similar to the bank's domain name before they are used
to spoof the bank's Web site. Banks can conduct this monitoring
in-house or can contract with third parties who provide monitoring
services.
Banks can encourage customers and consumers to assist in the
identification process by providing prominent links on their Web
pages or telephone contact numbers through which customers and
consumers can report phishing or other fraudulent activities.
Banks can also train customer-service personnel to identify and
report customer calls that may stem from potential Web-site attacks.
Return to
the top of the newsletter
FFIEC IT SECURITY
-
We continue our coverage of
the FDIC's "Guidance
on Managing Risks Associated With Wireless Networks and Wireless
Customer Access."
Risk Mitigation
Security should not be compromised when offering wireless
financial services to customers or deploying wireless internal
networks. Financial institutions should carefully consider the risks
of wireless technology and take appropriate steps to mitigate those
risks before deploying either wireless networks or applications. As
wireless technologies evolve, the security and control features
available to financial institutions will make the process of risk
mitigation easier. Steps that can be taken immediately in wireless
implementation include:
1) Establishing a minimum set of security requirements for
wireless networks and applications;
2) Adopting proven security policies and procedures to address the
security weaknesses of the wireless environment;
3) Adopting strong encryption methods that encompass end-to-end
encryption of information as it passes throughout the wireless
network;
4) Adopting authentication protocols for customers using wireless
applications that are separate and distinct from those provided by
the wireless network operator;
5) Ensuring that the wireless software includes appropriate audit
capabilities (for such things as recording dropped transactions);
6) Providing appropriate training to IT personnel on network,
application and security controls so that they understand and can
respond to potential risks; and
9) Performing independent security testing of wireless network and
application implementations.
Return to the top of
the newsletter
NATIONAL INSTITUTE OF STANDARDS
AND TECHNOLOGY -
We
continue the series on the National Institute of Standards and
Technology (NIST) Handbook.
Chapter 20 -
ASSESSING AND MITIGATING THE RISKS TO A HYPOTHETICAL COMPUTER SYSTEM
(HGA)
20.3.5 Network-Related Threats
Most of the human threats of concern to HGA originate from insiders.
Nevertheless, HGA also recognizes the need to protect its assets
from outsiders. Such attacks may serve many different purposes and
pose a broad spectrum of risks, including unauthorized disclosure or
modification of information, unauthorized use of services and
assets, or unauthorized denial of services.
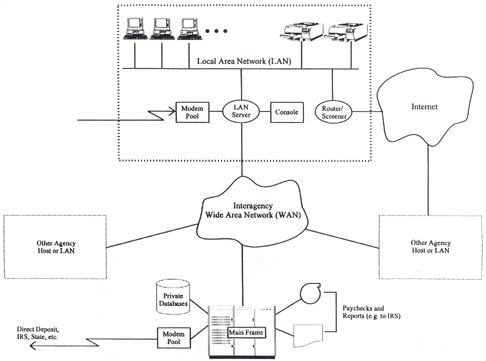
As shown in the figure
below, HGA's systems are connected to the three external networks:
(1) the Internet, (2) the Interagency WAN, and (3) the
public-switched (telephone) network. Although these networks are a
source of security risks, connectivity with them is essential to
HGA's mission and to the productivity of its employees; connectivity
cannot be terminated simply because of security risks.
In each of the past few
years before establishing its current set of network safeguards, HGA
had detected several attempts by outsiders to penetrate its systems.
Most, but not all of these, have come from the Internet, and those
that succeeded did so by learning or guessing user account
passwords. In two cases, the attacker deleted or corrupted
significant amounts of data, most of which were later restored from
backup files. In most cases, HGA could detect no ill effects of the
attack, but concluded that the attacker may have browsed through
some files. HGA also conceded that its systems did not have audit
logging capabilities sufficient to track an attacker's activities.
Hence, for most of these attacks, HGA could not accurately gauge the
extent of penetration.
In one case, an
attacker made use of a bug in an e-mail utility and succeeded in
acquiring System Administrator privileges on the server--a
significant breach. HGA found no evidence that the attacker
attempted to exploit these privileges before being discovered two
days later. When the attack was detected, COG immediately contacted
the HGA's Incident Handling Team, and was told that a bug fix had
been distributed by the server vendor several months earlier. To its
embarrassment, COG discovered that it had already received the fix,
which it then promptly installed. It now believes that no subsequent
attacks of the same nature have succeeded.
Although HGA has no
evidence that it has been significantly harmed to date by attacks
via external networks, it believes that these attacks have great
potential to inflict damage. HGA's management considers itself lucky
that such attacks have not harmed HGA's reputation and the
confidence of the citizens its serves. It also believes the
likelihood of such attacks via external networks will increase in
the future.
|
